You’ve written a variety of .NET apps and are running into problems connecting to a third party site using .NET as the client creating outbound requests.
This post is not about configuring your server to receive requests using TLS 1.1, and higher. If you are looking for configuring IIS, etc, to meet PCI DSS or other security requirements, go and get IIS Crypto from Nartec for free. No need to play around in the registry. It is a truly great tool that you can rely on and will pass external scanners like Qualys or Trustwave.
Let’s get started:
Windows 2012 R2 and Windows 2008 R2
In my case, I have a simple website which has it’s own sub-application (not just a virtual folder) which uses the DefaultAppPool which, in turn, uses .NET v4.0:
This particular app creates outbound HTTPS requests and gets an answer, as well as content. With the standard, out of the box installation, the connection will fail and be rejected because the host server is only set to allow TLS 1.1. and higher connections.
We need to tell Windows to allow higher connections and, in fact, default to them.
Ready? It is so easy:
Open regedit. There are two places you need to add a key to get get strong cryptography:
HKEY_LOCAL_MACHINE > SOFTWARE > Microsoft > .NETFramework > v4.0.30319
HKEY_LOCAL_MACHINE > SOFTWARE > Wow6432Node > Microsoft > .NETFramework > v4.0.30319
The new DWORD to add: SchUseStrongCrypto
And it’s value: 1 (or as it appears 00000001)
As you can see below, I have exported the keys with the new values added. AspNetEnforceViewStateMac is the default key that already exists.
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\.NETFramework\v4.0.30319] "AspNetEnforceViewStateMac"=dword:00000001 "SchUseStrongCrypto"=dword:00000001
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\.NETFramework\v4.0.30319] "AspNetEnforceViewStateMac"=dword:00000001 "SchUseStrongCrypto"=dword:00000001
Note: this appears to be a parent configuration for all the SKUs keys beneath this folder. I have NOT tested with other versions of .NET that are in the SKUs key folder. If something fails, simply add the key to each one you are using.
Here are some images to help you along:
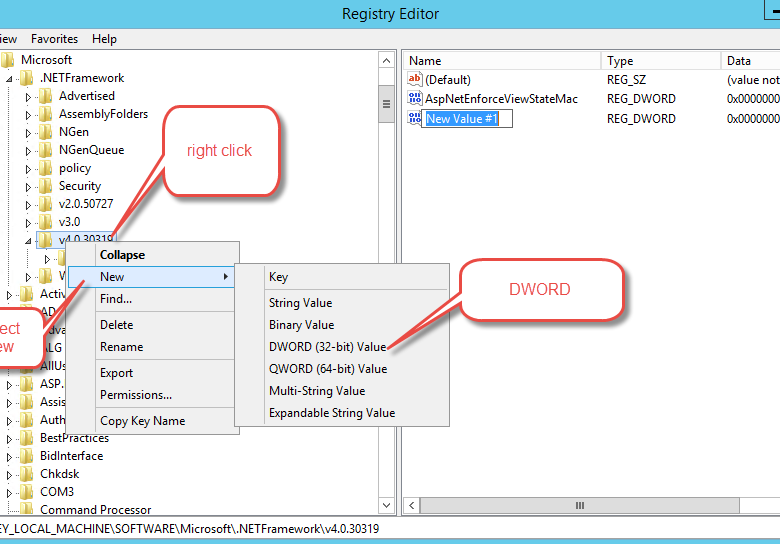
Have SchUseStrongCrypto already copied and ready to CTRL+v before you begin. Open regedit and scroll down to the first key HKEY_LOCAL_MACHINE > SOFTWARE > Microsoft > .NETFramework > v4.0.30319. Right click > New > DWORD (32-bit) Value. Paste SchUseStrongCrypto into where it says “New Value #1”. If you make a mistake, just delete the key, then try again.
Then right click > Modify.
Then simply change the default value of 0 to 1 and click Ok.
That’s it.
Reboot and you’re done!
Additional Information you might need
Handy URLs for testing. Each of the following that I got from here you can use to test different security cyphers with a WebRequest:
- SSL 2 (1995): not supported https://www.ssllabs.com:10200
- SSL 3 (1996): supported https://www.ssllabs.com:10300
- TLS 1.0 (1999): supported https://www.ssllabs.com:10301
- TLS 1.1 (2006): not supported https://www.ssllabs.com:10302
- TLS 1.2 (2008): not supported https://www.ssllabs.com:10303
More Windows information:
You may need to add/modify these keys.
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2] [HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Client] "DisabledByDefault"=dword:00000000 "Enabled"=dword:00000001 [HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Server] "DisabledByDefault"=dword:00000000 "Enabled"=dword:00000001




[…] Enable outbound TLS 1.1 and 1.2 on Windows Server […]